Ingecom distribuye las llaves de seguridad de autenticación por hardware de Yubico | Actualidad | IT Digital Security

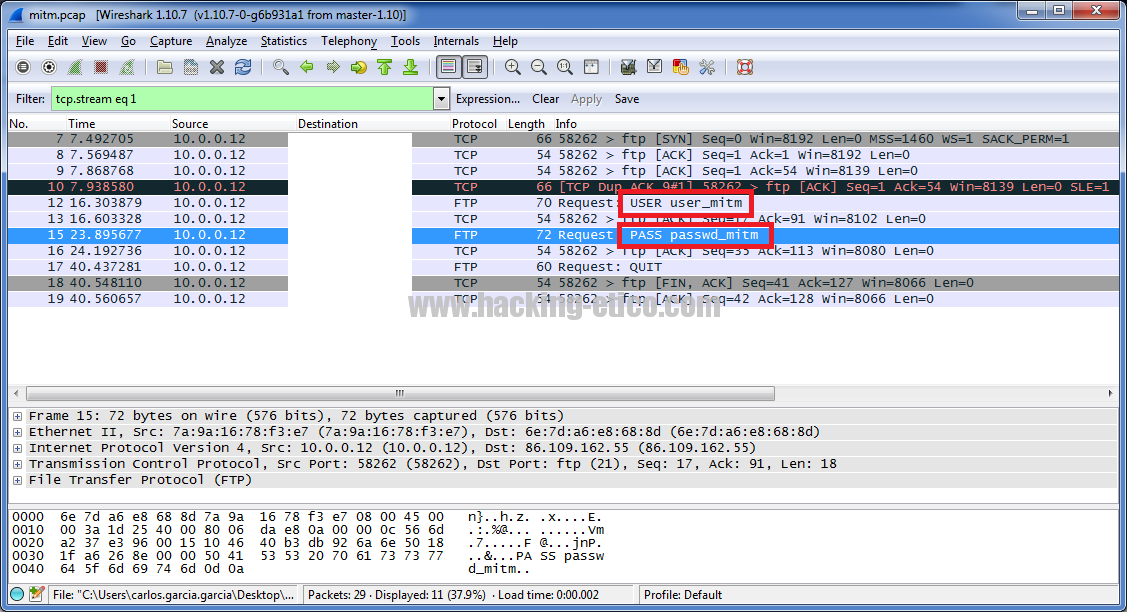
Null Byte & Null Space Labs Present: Wi-Fi Hacking, MITM Attacks & the USB Rubber Ducky « Null Byte :: WonderHowTo

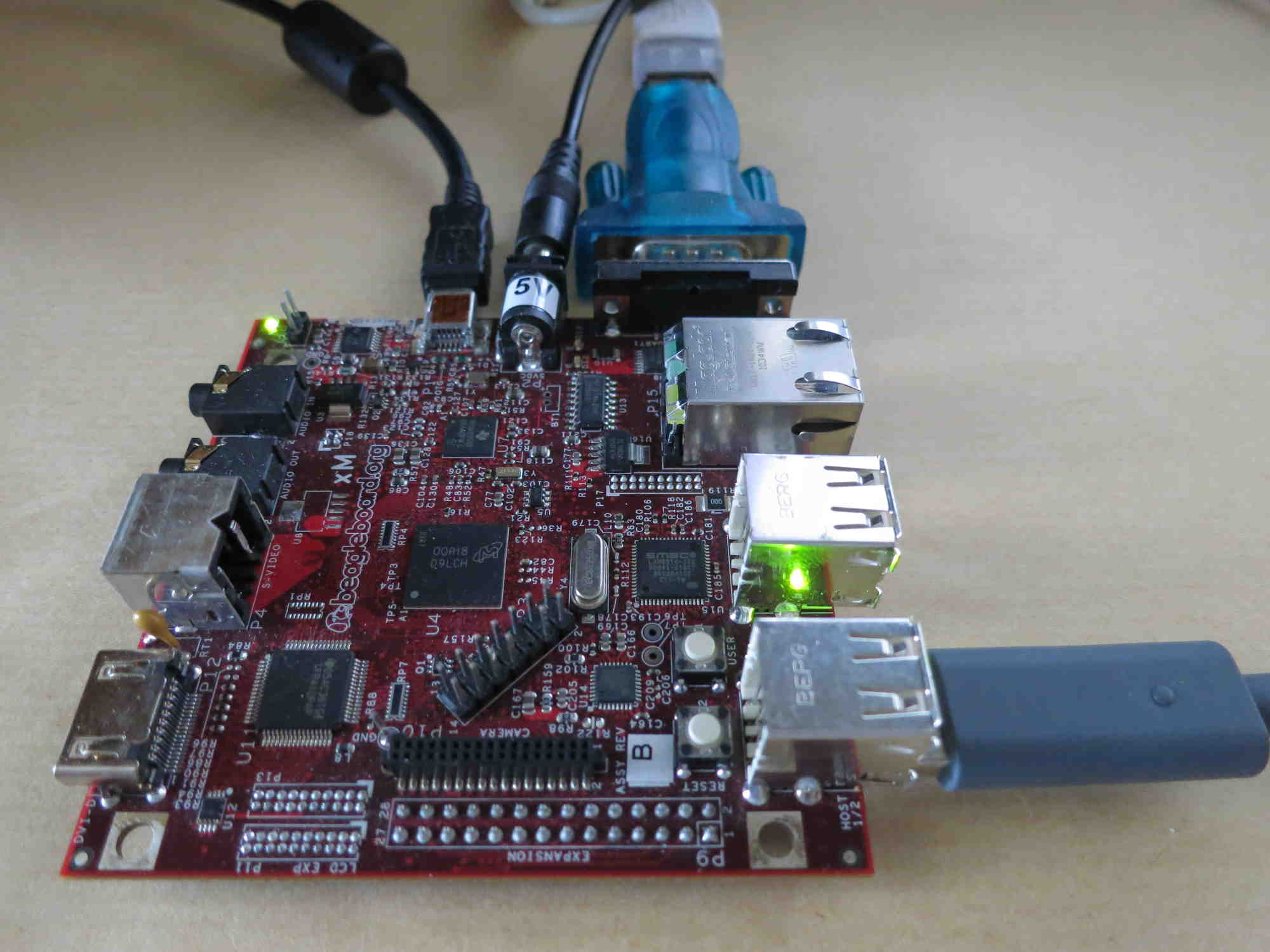
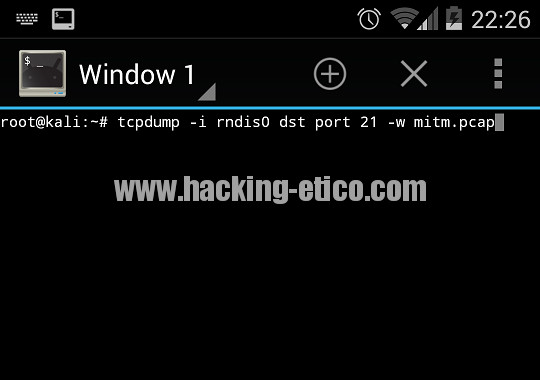
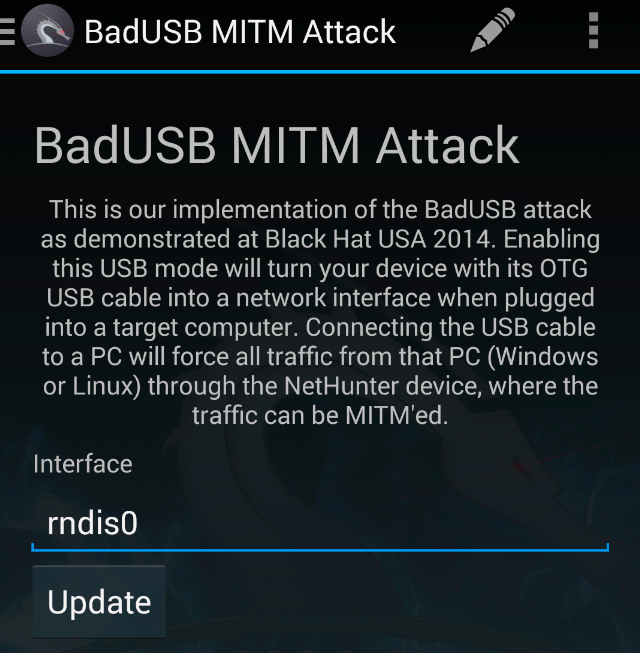
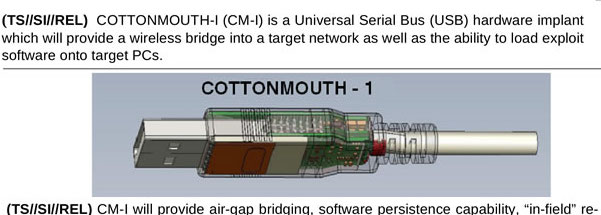
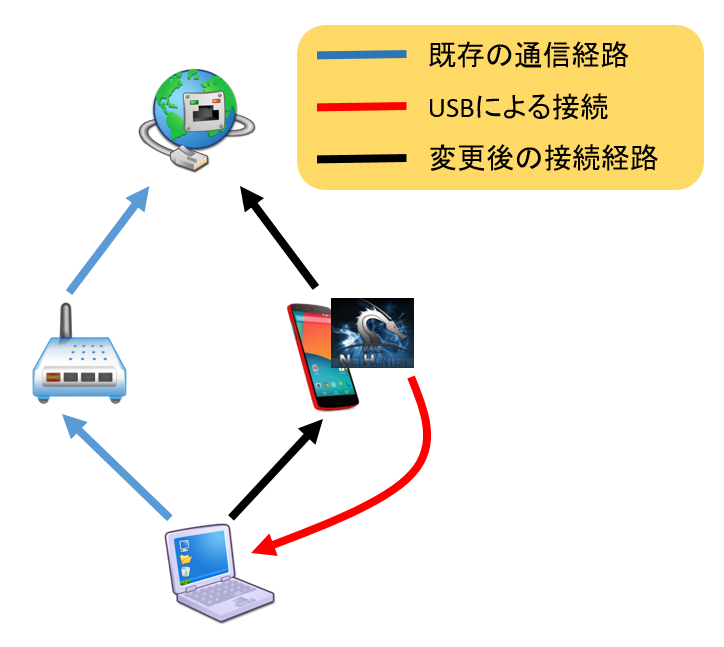
BadUSB 2.0 USB MITM POC. – Security List Network™ | Computer security, Cyber security, Hacking computer
GitHub - BenGardiner/USBProxy: A USB man in the middle device using USB On-The-Go, libUSB and gadgetFS

KeyGrabber Pico USB 16MB - Tiny Hardware USB Keylogger con 16 Megabyte Flash Drive : Amazon.es: Informática





![PDF] BadUSB 2 . 0 : USB man in the middle attacks | Semantic Scholar PDF] BadUSB 2 . 0 : USB man in the middle attacks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/907e8c34507e1d78f048abb26fa9c684097a562c/19-Figure3.1-1.png)